Teardrop Attack
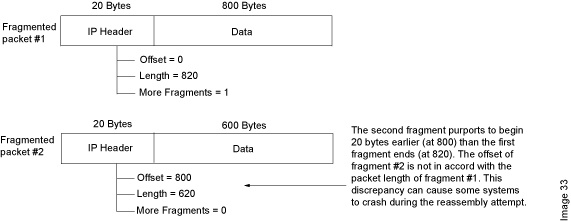
A teardrop attack is a denial-of-service (DoS) attack that involves sending fragmented packets to a target machine. Since the machine receiving such packets cannot reassemble them due to a bug in TCP/IP fragmentation reassembly, the packets overlap one another, crashing the target network device. This generally happens on older operating systems such as Windows 3.1x, Windows 95, Windows NT, and versions of the Linux kernel prior to 2.1.63One of the fields in an IP header is the “fragment offset” field, indicating the starting position, or offset, of the data contained in a fragmented packet relative to the data in the original packet. If the sum of the offset and size of one fragmented packet differs from that of the next fragmented packet, the packets overlap. When this happens, a server vulnerable to teardrop attacks is unable to reassemble the packets – resulting in a denial-of-service condition. Symptoms of Attack
When a Teardrop attack is run against a machine, it will crash (on Windows machines, a user will likely experience the Blue Screen of Death), or reboot. If you have protected yourself from the win nuke and sapping DoS attacks and you still crash, then the mode of attack is probably teardrop or land. If you are using IRC, and your machine becomes disconnected from the network or Internet but does not crash, the mode of attack probably clicks.
How can I fix this vulnerability?
If you are experiencing teardrop attacks on a Windows-based system, visit Windows Central’s teardrop page, or EFnet’s DoS Information Page to learn how to defend against this attack. If you are experiencing attacks on a Linux-based system, upgrade to version 2.0.32 / 2.1.63 or later.
Where can I read more about this?
The Teardrop attack is fairly well documented. Rootshell’s Teardrop page provides detailed technical specifications for the Teardrop program, as well as the source code. For a general overview of both the Teardrop and land DoS attacks, read CERT Advisory 97.28. Other very good sources for information on Teardrop, and other DoS attacks, include Ozemail’s DoS Site, IRChelp’s DoS Site, and CERT’s Advisory Site. In addition to the links listed above, a simple search of the Web, using Infoseek or Yahoo, should reveal a wealth of information on the Teardrop attack.
Definition – What does Teardrop Attack mean?
A teardrop attack is a denial of service (DoS) attack conducted by targeting TCP/IP fragmentation reassembly codes. This attack causes fragmented packets to overlap one another on the host receipt; the host attempts to reconstruct them during the process but fails. Gigantic payloads are sent to the machine that is being targeted, causing system crashes.
Techopedia Explains Teardrop Attack
While much more popular on older versions of Windows, is also possible on Windows 7 and Windows Vista machines that have SMB enabled. The driver vulnerability on the latter two operating systems was noted in 2009, but Windows 2000 and Windows XP are not vulnerable to this type of teardrop attack, which hones in on TCP ports 139 and 445 on the firewalls of the SMB-enabled machines. If users don’t have patches to protect against this DoS attack, SMBv2 should be disabled, as recommended by Microsoft, and ports 139 and 445 should be blocked.
We Provide Services In the Following Cities |
|||||
| *Ethical Haker in Ludhiana | *Ethical Hacking Services in Ludhiana | *Ethical Hacking Services in Mumbai | |||
|
|||||

